Cybersecurity lessons from practice
Companies increasingly feel unprotected from cyber attacks, according to recent Veeam Software research among 4,200 IT leaders. At Plate, we are aware of cyber threat and were recently victims of an automated cyber attack on our platform ourselves. We are happy to share our findings and learnings with you.
99.9 isn't a 100% uptime..
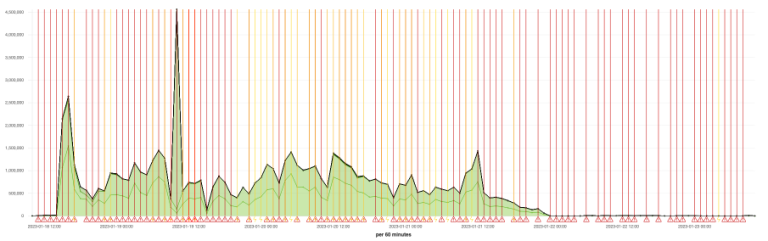
'Help, Plate is down.' On January 18, we experienced slowdowns on our servers starting in the late afternoon. A specific website on one of the servers is getting up to 4,500,000 requests per hour from that point on, 100 times more requests than normal. We have been targeted by a DDos attack. Below you can see the load on our server from the start to the end of the attack. Note that our uptime measured over a year is still 99.9%.
How does a DDos attack work?
A DDoS attack (Distributed Denial of Service attack) is an attack on a network or server that generates large amounts of traffic from various sources (usually infected computers or "bots") to reduce or interrupt the availability of a specific Web site or service. This can be done by overloading traffic or by exploiting specific weaknesses in a system. DDos is a form of cybercrime.
How did we manage to stop the DDos attack?
Our automatic and self-learning firewall PAS blacklists IP addresses where the traffic comes from, but the attackers manage to circumvent the blockade with new IP addresses each time. The attack slowly weakens, but continues through Saturday night after which the DDos stops at exactly 00:00. Calm has returned.
Our next step is to check why a blocked DDOS attack could still have so much impact, and put in an extra layer of defense for that. Because, of course, we want to be able to withstand even the biggest attacks with our platform.
What have we learned?
In addition to the technical steps we have taken - and will take - we have also learned that clear communication is crucial. It is essential to inform and reassure customers that we are doing everything we can to fix the problem as quickly as possible.
Below are some concrete communication lessons we have learned:
- Designate a person responsible for communication during an outage,
- Work with a central status page where you clearly communicate what is going on and provide regular status updates during the cyberattack.
There should be a process and plan in place what goes into effect during a cyberattack and what you can fall back on. This states how your organization will act during an attack or data breach and divides the actions and responsibilities. Plate lacked an established process, so we were busy solving the outage but forgot to share status updates, for example.
We took immediate action and made work of a clear status page that includes space for updates during outages. For the current status of our servers visit status.getplate.com.
Over the next few weeks, we are working on a tightened-up version of our Cyber Incident Response Plan that further details the process of how we at Plate deal with a cyber attack or data breach and the steps we take to mitigate the impact.
What are we doing about cybersecurity at Plate?
At Plate, we take the security and uptime of the websites, apps and portals on our platform extremely seriously. This is also why we invest a lot of time and knowledge to be at the forefront of this. Especially since Plate is a hosted CMS, which means we take care of the uptime and technical operation of the platform, our customers and partners expect a lot from us. And because cybersecurity is a constantly changing discipline, it comes with trial and error as you read above.
PAS
In partnership with Securely, we introduced PAS (Plate Artificial Security) in early 2022. PAS acts as Plate's immune system, repelling attacks 24/7. Because PAS is self-learning, it grows with changing environments. Read more about PAS.
Autoscaling
Autoscaling is a technique we use to automatically adjust the capacity of a system according to the amount of traffic it receives. In our CMS, where multiple users or clients use the same infrastructure (multi-tenant), autoscaling is used to increase or decrease server capacity based on the current load.
For example, if a site receives a lot of traffic, autoscaling can automatically add additional servers to the system to handle this traffic. On the other hand, if a site receives less traffic, autoscaling can automatically remove servers from the system to save costs.
Plate Private Clusters (PPC)
For customers with high traffic or high peaks, we can place the websites running on Plate on their own AWS cluster. For this, we set up infrastructure specifically for the customer that we can also fine-tune for the characteristics of usage. As a result, sites are typically faster and have even higher uptime (during the recent DDos attack, the Private Clusters were just online!).
What can you do yourself to protect against cyber threat?
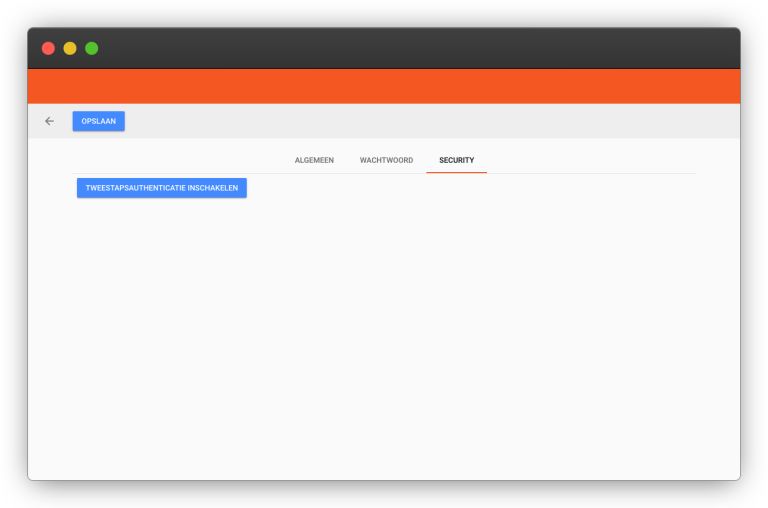
Even personally, you face the dangers of cyberthreats. How often do you get phishing emails with ransomware that hackers use to try to access your data? To protect your websites and data within Plate, we offer an option to secure your Plate account with Two Step Authentication (2FA). This means that when you log in, you must enter an additional code to actually be logged in.
If you want to use 2FA, click from your Plate account on 'User settings' > 'Security' > 'Enable two-step authentication'.
We have shown you in this article what the impact of a cyber-attack is and the lessons learned. Cyber attacks are a social problem costing companies and governments billions every year. Insurers are even warning that cybersecurity will soon be harder to insure than climatic damage (Dutch article).
As a SaaS company, we are aware of our vulnerable position, but we want to avoid making cyber threats a taboo subject. Instead, companies need to learn much more from each other when it comes to security incidents.
Do you have experiences with cyber attacks and want to share them with us? Send an email to david@getplate.com and we would be happy to chat with you about this hot topic.